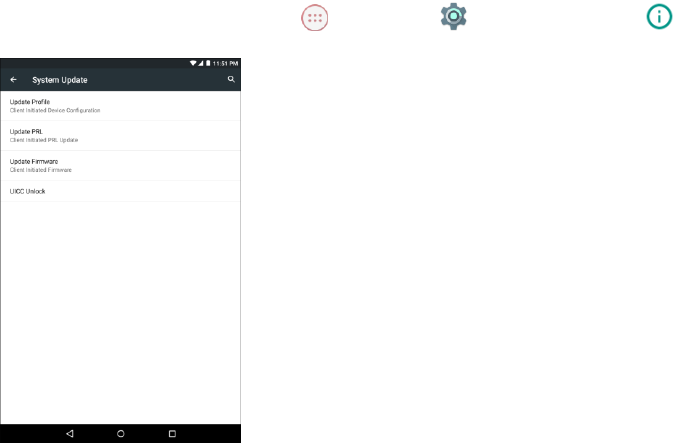
Uicc Unlock From System Updates Menu
Design Doll Cracked.Lil Wayne – Tha Carter II / Tha Carter 2 – Album Quality: iTunes Plus AAC M4A Download Free Zippyshare Batshare Sharebeast Released: December 6, 2005 ℗ Cash Money, Young Money, Universal Tha Carter II is the fifth studio album by American rapper Lil Wayne, released on December 6, 2005 in the United States. System Update Option Description; Update Profile. Update your user profile information. Update the latest PRL (Preferred Roaming List) used by your tablet to access the network. Update Firmware. Download and update the firmware for your tablet. Unlock your tablet's UICC (Universal Integrated Circuit Card). Here is a list of devices that are part of our Bootloader Unlock program. Check back often as we add new unlockable devices. If your device is not listed below, feel free to visit here and follow the process to see if it is unlockable. SOFTWARE UPDATES. Software Upgrade Schedule. Here is a list of devices that are part of our Bootloader Unlock program. Check back often as we add new unlockable devices. If your device is not listed below, feel free to visit here and follow the process to see if it is unlockable.
Tutorial to Unlock Sprint Galaxy Note 3 For T-Mobile/AT&T/MVNO's Tools required: Hidden Menu Enabled(modified for galaxy note 3): http://goo.gl/y4k2EG MI3 modem (modified to be flashed via odin): http://goo.gl/W0f3Za Odin 3.07 or 3.09 (google for it theres a million mirrors of it) Device must already be internationally unlocked via sprint for this to work (must perform uicc unlock from system updates menu) im working on a way to do this without sprint but for now this is how it is) Region Lock Away: (Free on chainfires thread or consider buying market donate version) http://forum.xda-developers.com/show....php?t=2470551 Device must be rooted: (rooting via this method will trip knox however the modem flash we have to do will likely trip it as well): http://download.chainfire.eu/362/CF-...pr-smn900p.zip Any root browers from play store ServiceMode Shortcut: Grab from play store prl helper or anything with an apn shortcut: Grab from play store Step 1: We need to root the device so put device in download mode holding vol down+home+power while it is off. Flash cf auto root to obtain root (this will void knox). Step 2: Grab a root browser, ServiceMode Shortcut, PRL Helper, and Region Lock Away and install your att/tmobile sim. Step 3: Place device back into download mode. PAY ATTENTION HERE: you need to add the mi3 modem to pda and uncheck auto reboot. LEAVE ON F. RESET TIME CHECKED. After flash has completed remove battery from your phone place it back into download mode and flash mi3 modem again this time leaving auto reboot checked. When your device boots up to to settings->general->about device and check your baseband version to make sure it ends in mi3. if it does not redo step 3. Step 4: Run regionlock away (not required for this all to work just for good measure), And switch your device into gsm/umts only mode in your settings menu. Step 5: Plug your device in and enable usb debugging. run hidden menu enabler. open TestMode Menu. Follow these steps perfectly. 1. click ue setting and info 2. click setting 3. click protocol 4. click as- go to security control and make sure fake security is on, ciphering is off, and integrity is on. after you have seet these hit menu back twice to get back to ue setting and protocol menu. 5. open nas-go to network control go to band selection and pick number 5 wcdma/gsm mode only. after hit menu back. 6. Click pref mode set and choose number 2 gsm wcdma only. menu back once 7.hit aquision order and choose umts_gsm. hit menu back until youre back at ue setting menu. 8. open gcf and click number 1 and make sure it is on. hit menu back to ue settings. 9.go to sim and then sim class control. make sure umts on and gsm on both show. if not click to enable. hit menu back once 10.hit bip block control. hit number 3 bip block off. once complete go to bip block status to verify it is in fact off. 11. go all the way back to main menu. hit protocol state, sim information, check nv, and make sure it shows sim lock is disable, spr bip unblocked, and sha256 on or off shouldnt matter. ( i have had mine off and on and it seems to work either way)(mine is currently on) 12. power cycle device. 13. when it comes on device SHOULD show service it still may not. 14. get into your root browser, go system, and open your build.prop with a text editor 15. add these lines to the very bottom to enable apn editing. (credit to ingenium13) ril.sales_code=LOL ro.csc.sales_code=LOL 16. reboot device once more. now use prl helper or your apn shortcut and create a new apn for your carrier. delete all the sprint ones and make sure you highlight the circle next to your newly created apn. reboot once more. 17. device should come up with full service bars and data/mms active. (if you have an inactive sim card it does not always show service)(my inactive att card would show service my inactive tmobile would not) 18. Donations appreciated now you should be 100% unlocked. if you need to undo this for any reason see post 3 to get fully back on sprint. 19. Profit! |
Android 5.1 introduced a mechanism to grant special privileges for APIsrelevant to the owners of universal integrated circuit card (UICC) apps. TheAndroid platform loads certificates stored on a UICC and grants permission toapps signed by these certificates to make calls to a handful of special APIs.
Android 7.0 extended this feature to support other storage sources for UICCcarrier privilege rules, dramaticallyincreasing the number of carriers that can use the APIs. For an API reference,see CarrierConfigManager; for instructions,see CarrierConfiguration.
Carriers have full control of the UICC, so this mechanism provides asecure and flexible way to manage apps from the mobile network operator (MNO)hosted on generic app distribution channels (such as Google Play) whileretaining special privileges on devices and without the need to sign apps withthe per-device platform certificate or preinstall as a system app.
Rules on UICC
Storage on the UICC is compatible with theGlobalPlatformSecure Element Access Control specification. The application identifier(AID) on the card is A00000015141434C00, and the standardGET DATAcommand is used to fetch rules stored on the card. You may update these rulesthrough card over-the-air (OTA) updates.
Data hierarchy
UICC rules use the following data hierarchy (the two-character letter andnumber combination in parentheses is the object tag). Each rule isREF-AR-DO (E2) and consists of a concatenation of REF-DO and AR-DO:
REF-DO(E1) containsDeviceAppID-REF-DOor a concatenation ofDeviceAppID-REF-DOandPKG-REF-DO.DeviceAppID-REF-DO(C1) stores the SHA-1 (20 bytes) or SHA-256 (32 bytes) signature of the certificate.PKG-REF-DO(CA) is the full package name string defined in the manifest, ASCII encoded, max length 127 bytes.
AR-DO(E3) is extended to includePERM-AR-DO(DB), which is an 8-byte bit mask representing 64 separate permissions.
If PKG-REF-DO isn't present, any app signed by the certificateis granted access; otherwise both the certificate and the package name need tomatch.
Rule example
The app name is com.google.android.apps.myapp and theSHA-1 certificate in hex string is:
The rule on UICC in hex string is:
Access rule file (ARF) support
Android 7.0 adds support for reading carrier privilege rules from the accessrule file (ARF).
The Android platform first attempts to select the access rule applet (ARA)application identifier (AID) A00000015141434C00. If it doesn't findthe AID on the UICC, it falls back to ARF by selecting PKCS15 AIDA000000063504B43532D3135. Android then reads theaccess control rules file (ACRF) at 0x4300 and looks for entrieswith AID FFFFFFFFFFFF. Entries with different AIDs are ignored, sorules for other use cases can co-exist.
Example ACRF content in hex string:
Example access control conditions file (ACCF) content:
In the example above, 0x4310 is the address for ACCF, whichcontains the certificate hash61:ED:37:7E:85:D3:86:A8:DF:EE:6B:86:4B:D8:5B:0B:FA:A5:AF:81. Appssigned by this certificate are granted carrier privileges.
Enabled APIs
Android supports the following APIs.
TelephonyManager
- Method to allow the carrier app to ask UICC for a challenge/response:
getIccAuthentication. - Method to check whether the calling app has been granted carrierprivileges:
hasCarrierPrivileges. - Methods to override brand and number:
- Methods for direct UICC communication:
- Methods to set device mode to global:
setPreferredNetworkTypeToGlobal.
SmsManager
Method to allow caller to create new incoming SMS messages:injectSmsPdu.
CarrierConfigManager
Method to notify configuration changed:notifyConfigChangedForSubId. For instructions, seeCarrier Configuration.
CarrierMessagingService
Service that receives calls from the system when new SMS and MMS are sentor received. To extend this class, declare the service in your manifest filewith the android.Manifest.permission#BIND_CARRIER_MESSAGING_SERVICEpermission and include an intent filter with the #SERVICE_INTERFACEaction. Methods include:
Telephony provider
Content provider APIs to allow modifications (insert, delete, update, query)to the telephony database. Values fields are defined atTelephony.Carriers; for more details, refer toTelephony API reference on developer.android.com.
Android platform
On a detected UICC, the platform constructs internal UICC objects thatinclude carrier privilege rules as part of the UICC.UiccCarrierPrivilegeRules.javaloads rules, parses them from the UICC card, and caches them in memory. Whena privilege check is needed, UiccCarrierPrivilegeRules compares thecaller certificate with its own rules one by one. If the UICC is removed, therules are destroyed along with the UICC object.
Validation
The Compatibility Test Suite (CTS) includestests for carrier APIs inCtsCarrierApiTestCases.apk. Because this feature depends oncertificates on the UICC, you must prepare the UICC to pass these tests.
Preparing the UICC
By default, CtsCarrierApiTestCases.apk is signed by Androiddeveloper key, with hash value61:ED:37:7E:85:D3:86:A8:DF:EE:6B:86:4B:D8:5B:0B:FA:A5:AF:81. Thetests also print out the expected certificate hash if certificates on UICCmismatch.
Example output:
In order to validate the implementation through CTS usingCtsCarrierApiTestCases.apk, you must have a developer UICC withthe correct UICC rules or ARF support. You may ask the SIM card vendorof your choice to prepare a developer UICC with the right ARF as described inthis section and use that UICC to run the tests. The UICC doesn't requireactive cellular service to pass CTS tests.
Running tests
For convenience, CTS supports a device token that restrictstests to run only on devices configured with same token. Carrier API CTS testssupport the device token sim-card-with-certs. For example, thefollowing device token restricts carrier API tests to run only on deviceabcd1234:
When running a test without using a device token, the test runs on alldevices.
FAQ
How can certificates be updated on the UICC?
A: Use the existing card OTA update mechanism.
Can UICC co-exist with other rules?
A: It's fine to have other security rules on the UICC under same AID; theplatform filters them out automatically.
What happens when the UICC is removed for an app that relies on thecertificates on it?
A: The app loses its privileges because the rules associated with theUICC are destroyed on UICC removal.
Is there a limit on the number of certificates on the UICC?
A: The platform doesn't limit the number of certificates; but because thecheck is linear, too many rules may incur a latency for check.
Is there a limit to the number of APIs that we can support with thismethod?
A: No, but we limit the scope to carrier-related APIs.
Are there some APIs prohibited from using this method? If so, how doyou enforce them? (that is, do you have tests to validate which APIs aresupported with this method?)
A: See the 'API Behavioral Compatibility' section of theAndroid Compatibility DefinitionDocument (CDD). We have some CTS tests to make sure that the permissionmodel of the APIs isn't changed.
How does this work with the multi-SIM feature?
A: The default SIM specified by the user is used.
Does this in any way interact or overlap with other SE accesstechnologies, for example, SEEK?
A: As an example, SEEK uses the same AID as on the UICC. So the rulesco-exist and are filtered by either SEEK or UiccCarrierPrivileges.
When is it a good time to check carrier privileges?
A: After the SIM state loaded broadcast.
Can OEMs disable part of carrier APIs?
A: No. We believe that the current APIs are the minimal set, and weplan to use the bit mask for finer granularity control in the future.
Does setOperatorBrandOverride override ALL other forms of operatorname strings? For example, SE13, UICC SPN, or network-based NITZ?
A: Refer to the SPN entry inTelephonyManager
Uicc Unlock Boost Code
What does the injectSmsPdu method call do?
A: This method facilitates SMS backup/restore in the cloud. TheinjectSmsPdu call enables the restore function.
For SMS filtering, is the onFilterSms call based onSMS UDH port filtering? Or do carrier apps have access to ALL incoming SMS?
A: Carriers have access to all SMS data.
The extension of DeviceAppID-REF-DO to support32 bytes appears to beincompatible with the current GP spec (which allows 0 or 20 bytes only), so whyare you introducing this change? Isn't SHA-1 sufficient toavoid collisions? Have you proposed this change to GP already, as this couldbe backward incompatible with existing ARA-M/ARF?
A: For providing future-proof security, this extension introduces SHA-256for DeviceAppID-REF-DO in addition to SHA-1, which is currentlythe only option in the GP SEAC standard. We highly recommend using SHA-256.
If DeviceAppID is 0 (empty), do you apply the rule toall device apps not covered by a specific rule?
A: Carrier APIs require DeviceAppID-REF-DO be populated.Being empty is intended for test purposes and isn't recommended for operationaldeployments.
Uicc Unlock From System Updates Menu Free
According to your spec, PKG-REF-DO used just by itself, without DeviceAppID-REF-DO, shouldn't be accepted. Butit's still described in Table 6-4 as extending the definition ofREF-DO. Is this on purpose? How does the codebehave when only PKG-REF-DO is used in REF-DO?
A: The option of having PKG-REF-DO as a single value item in REF-DO was removed in the latest version. PKG-REF-DO should only occur in combination with DeviceAppID-REF-DO.
We assume that we can grant access to all carrier-based permissionsor have finer-grained control. If so, what defines the mapping between the bitmask and the actual permissions? One permission per class? One permission permethod? Are 64 separate permissions enough in the long run?
A: This is reserved for the future, and we welcome suggestions.
Can you further define DeviceAppID for Androidspecifically? This is the SHA-1 (20 bytes) hash value of the Publishercertificate used to signed the given app, so shouldn't the name reflect thatpurpose? (The name could be confusing to many readers as the rule is thenapplicable to all apps signed with that same Publisher certificate.)
Uicc Unlock Authentication Error
A: The DeviceAppID storing certificates is supported by the existing spec. We tried to minimize spec changes to lower the barrier for adoption. For details, see Rules on UICC.
